Trustwave & RMI Collaboration – Threats to the Energy Industry
With subject matter expertise and presence across the globe, RMI Global Solutions are recognized by the oil & gas, and broader energy industry on and offshore, as experts in the threats and risks that face the spectrum of this key industry worldwide. RMI has significant provenance in the delivery of intelligence & security solutions for businesses operating across the energy industry and are working across many clients. Given our recognized expertise, energy-body groups such as the International Association of Drilling Contractors (IADC), National Ocean Industries Association (NOIA), and Offshore Energy UK (OEUK) repeatedly call on RMI to present updates on the threat and mitigation strategies to their members. Trustwave and RMI are close partners in this enterprise, leveraging and coordinating our individual expertise for energy clients.
This short discourse is intended to compliment Trustwave’s position as “the most trusted cybersecurity leader by industry analysts” with this paper contextualising whom, where, and how the most significant broader threats manifest.
The Threat in Context:
The security envelope for the energy industry is deteriorating markedly, with little to suggest these threats and associated risks will decrease as we move into the third geo-political era of recent history: The Cold War ~ Hyper Globalization ~ and now, a period of competition just below the threshold of war between Autocracies and Democracies. Hostile state and non-state activity can be identified everywhere, alongside criminality, cartels & gangs and piracy; often working symbiotically and hidden in plain sight sometimes conducting legal or harmless activity, but frequently Probably conducting reconnaissance or setting conditions for future acts of general criminality, sabotage, or worse. Much of this malign activity Highly Likely emanates from state-based actors, with Russia being the most prevalent, frequently demonstrating its global reach; with additional regional activity controlled and delivered by a diverse range of similar autocratic powers, most notably Iran, North Korea, Venezuela, and Cuba. With China the other pan-global autocratic behemoth. However, given its economic power and reach its malign activities and actions are often more difficult to quantify but are as real and present a danger as those posed by Russia and its acolytes.
Unlike many other industries, the hydrocarbon extraction and processing element of the energy industry is increasingly exposed to the negative views and actions of protest groups opposed to fossil fuel use. Whilst many of these parties operate entirely legally, with their views underpinned by science around climate change, the more extreme elements have become far more strident in the direct actions they are prepared to take. Some are Almost Certainly encouraged by malign state-actors, others self-radicalized via the internet and other fora. But what is most concerning is where their activity might go. Posting negative comments on the internet can rapidly develop to direct action, including cyber-attacks, but at its most extreme, there is the possibility of direct action to attack or assassinate individuals such as happened to the CEO of the U.S. health insurer UnitedHealthcare, another “contentious and unpopular industry.” He was murdered in Manhattan on 4th December by a radicalized individual, who has subsequently been lionized across the darker reaches of the internet, making similar copycat attacks more Likely.
Developing Technologies and Tactics – Particularly Drones
The most notable shift in attack methodology against the oil industry occurred on 14th September 2019, when Iranian-backed Houthi rebels launched a coordinated drone and missile attack on Saudi Aramco’s Abqaiq processing plant and Khurais oil field. This attack temporarily halted half of Saudi Arabia’s oil production and resulted in a 20% spike in oil prices, at the time, the biggest single-day oil price increase in history. But the first weaponized use of unmanned aerial vehicles (UAV) or ‘drones’ was the most technologically noteworthy aspect of the attack.
Since this ‘first use’ the availability of UAV’s has increased exponentially, with Chinese manufacturers such as DJI dominating the market, and small commercial drones available virtually anywhere and at little cost, with 3D printing and local manufacturing making their availability even more ubiquitous. UAV use has been further brought into stark focus in the Ukraine/Russia war, with the internet full of images of small drones with explosives causing significant local damage, destroying vehicles, or killing individual soldiers. RMI are also aware of terrorists and pirates also now using drones in the Red Sea and in Southeast Asia to conduct reconnaissance of vessels they may wish to attack and to identify what security measures are in-place and how vulnerable they are to boarding.
These technologies and tactics are causing significant concern in the energy industry, which has long enjoyed “security by isolation” often operating far from shipping lanes or other potential access by humans. Now in a noticeably brief time, bad actors have seen how these UAV can be launched, often at significant reach, from ‘innocent’ fishing or leisure vessels to reconnoitre, disrupt or even in future attack energy platforms and vessels. The UK and Norwegian governments have both issued specific guidance over the reporting of these incidents, which are increasing in regularity. Beyond the physical threat a drone poses, either smashing into a platform with an explosive charge, dropping ‘white powder’ – which would need to be treated as a biological attack, or interfering with helicopter operations and making sustainment more difficult, they are also an ideal vehicle to deliver a cyber payload given the proximate access to a platform’s systems they can provide.
Going forward, and again partly because of military innovation during on-going conflicts in Ukraine and the Middle East, 2025 will Almost Certainly see more use of Uncrewed Surface Vehicles (USV) – a waterborne drone, and Uncrewed Underwater Vehicles (UUV) – a submarine drone. Again, the potential impact on the energy industry is significant, particularly given their relative size, and increased payloads which can cause much more damage. The Ukrainians have successfully destroyed Russian gas platforms in the Black Sea using USV/UUV, and others will have taken note – including pirates operating across the world. If a bad actor wants to do significant physical damage or destruction at sea, the USV or UUV would be ideal.
The drone, in all its various forms will continue to be a potent threat vector to the energy industry across 2025, particularly when their use is coordinated with cyber effects. This is most significant given the physical dislocation of most energy infrastructure, particularly offshore, away from a rapid, effective response force. Unless the energy industry begins to incorporate effective detect and defeat counter-UAV/USV/UUV measures they will be very vulnerable to this increasing threat vector, with little or no effective response on site or close by.
Espionage, Sabotage, and Insider Threats
When considering all of the above, and particularly the emphasis that state-based malign actors will place on disrupting any activity that is critical to the ‘West’s’ way of life, with energy an easy target that will cause much disruption if attacked, it’s important to consider the impact of espionage, sabotage and insider threats.
Throughout 2024, there has been a raft of arrests and convictions across Europe and the U.S. of individuals providing material support to Russia and China – as spies, collecting and then passing information to their agent handlers. Most of those identified by police, security and intelligence agencies were working across the West’s military industrial complex and academic institutions, but it would be naïve to believe that similar individuals are not already embedded across the energy industry. Even the most cursory examination of the 2021 cyber-attack on Colonial Pipeline shows a clear link to Russia via the DarkSide Ransomware-as-a-Service (RaaS) group. The six-day shutdown of Colonial Pipeline had a significant impact on the U.S. economy and caused panic buying and fuel shortages along the east coast of America. For as long as the U.S. and its allies remain in competition with Russia and China, acts of espionage will continue to be a threat across the spectrum of Western national interests, with embedded cells Highly Likely ready to be activated at the most inconvenient and damaging moments – of their choosing. The pervasive threat from espionage is protected by the secret nature of associated operations to counter it, meaning that any potential damage caused will Probably only become known once an adversary has successfully evaded detection and conducted an attack.
Sabotage, in all its forms continues to be a threat, particularly for an industry reliant on pipes and cables, either on the seafloor and above ground on land to move oil, gas and electricity. The significant distance these routes cover makes it almost impossible for security systems to cover their entire length and ID bad actors. The recent attacks on the Nord Stream gas pipeline running under the Baltic Sea in September 2022 by underwater demolition experts and a Chinese ship with a Russian Captain dragging its anchor to sever submerged internet cables in November 2024, also in the Baltic Sea are both good examples of the spectrum of sabotage facing the energy industry.
It is noteworthy to also consider that Russia maintains a specialist Military Intelligence unit, Glavnoye Upravelenie Glubokovodnykh Issledovanii (GUGI), which is trained and equipped to conduct operations at depths of up to 20,000 ft to identify then sever or breach cables and pipelines. Consequently, sabotage can no longer be discounted as a threat that ended when the Cold War finished in the early 1990s. But alongside a revanchist Russia, low-level sabotage from protest groups, subversives and the radicalized, all able to harness the power of the internet to enable their attacks will be another, Probably more prevalent sabotage risk in the next twelve months – and the hydrocarbon industry is a prime target.
The threat from insiders is often frequently considered from the perspective of their ability to act as a ‘Trojan Horse’ for a cyber-attack, either sharing passwords with bad actors or delivering a cyber payload from a 3rd party device such as a USB memory stick, or even a colleague whose poor password hygiene increases the risk of attack. But insiders can be far more than this and could enable all the activity discussed in this report, embedding themselves deep into an organization and its processes, able to provide an adversary – either a commercial rival or a state-based actor, with a trove of information to be used against its target at a time or place of their choosing. Employment practices such as increasing use of contractors, many of whom will sub, and then sub-contract, often without rigorous HR oversight and vetting regimes that are both costly and intrusive, often ignored or pared back to a point of being barely credible increase these risks. In some instances, they are exacerbated by a lack of cultural reinforcement over reporting colleagues for suspicious activity and not allowing lone workers in sensitive areas, particularly when employing non-core staff or contractors in these positions.
Summary
The points discussed above serve to highlight several of the most significant threats facing the energy industry in 2025. But this only provides a summary of what exists. Understanding the threat, be that from cyber-actors, or the vectors and methodologies discussed here requires deep subject matter expertise. As experts in our respective fields RMI and Trustwave can help you navigate the intricacies of an increasingly complex and complicated world, enabling your activity by deconstructing these threats and advising you on credible and cost-effective mitigation measures.
RMI Head of Intelligence, 14th January 2025
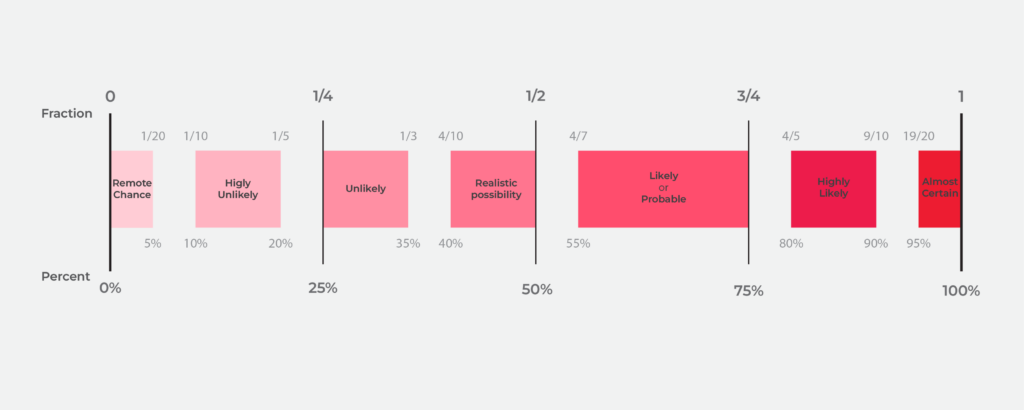
RMI Probability Yardstick